Author
Filippo Moriggia
After more than 10 years of experience in the technical journalism with PC Professionale (the italian version of PC Magazine) and other newspapers of Mondadori group, Filippo Moriggia founded GURU advisor, the reference website for IT professionals, system integrators, cloud providers and MSPs. He has a Master of Science in Telecommunications Engineering and works as a independent consultant and contractor for different firms. His main focuses are software, virtualization, servers, cloud, networking and security. He's certified VMware VCA for Data Center Virtualization.
If you carefully read the several interviews we had during the Mobile World Congress, you’ll notice for sure a thin fil-rouge between most of them: the attention to security-related matters.
In a world that is eternally and constantly interconnected there are no passwords, firewalls or ciphering algorithm that can always and anyhow guarantee data security. Similarly to the protection of a house, alarms, doors, gratings and the most sophisticated anti-intrusion systems may not be enough to guarantee protection if criminals know that between the walls, suitcases full of money or gold bar are waiting for them.
We must then live together with the idea that data is safe - at the moment - but it may not be like this when one of the protection we are currently employing gets obsolete or not anymore updated so that it can protect us.
And like in the best action movies we'll find at the end that it might not be a mistake of the smith while mounting gratins or a software bug in the control unit of our alarm to break into our defense line, but it’s rather a “social” fault: a relative that leaves unguarded the house keys, a distracted, gull house maid, or maybe a teenage daughter that has a crooky boyfriend.
In the IT world equilibrium is changing because our data is getting suddenly precious. In some cases data is meaningful only to us or to our company, but still has a value to the point that we are ready to pay a few hundreds of euros to have them back. Or some thousands of euros or even more. Unfortunately those who develop ransomware, a topic we have extensively covered in this number, have already understood that. And because of that they are involving a myriad of resources in this field, working both on the technical side and on the social side. Because there is a concrete and precise objective. Your money.
In order not to leave you and your company or clients at the mercy of some Russian boy, do something. Get informed, study, change your strategies, enforce your gratings and teach your employees. This is the only way to secure your data.
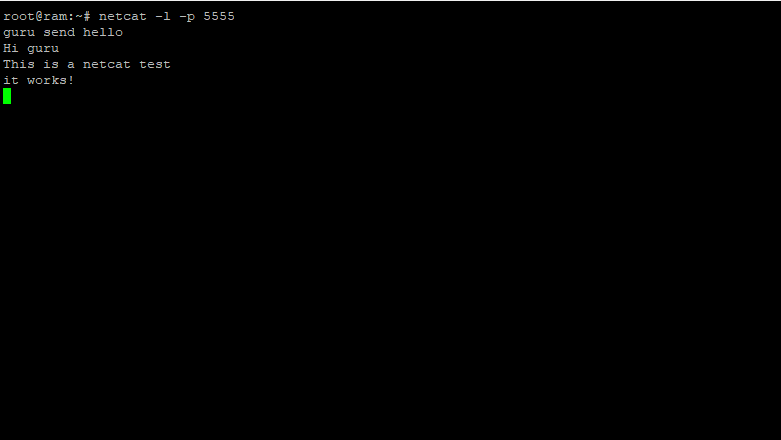
When preparing this article we’ve asked to all the main security firms to explain which technologies or tools they offer for ransomware protection. Common signature-based antiviruses are not enough to be protected as these malware are custom-tailored for every attack and the executable is masked and modified in different ways, so that it always appears as a different version.
You already know the most obvious advice: keep Windows, antivirus and all the main software (including tools like Flash, Java and Adobe Reader which are often an attack medium) up to date.
Let’s see what information we have collected from the security firms that have replied us.
Avast, mostly known for its antivirus, talked with us about DeepScreen: this technology, part of all desktop products since the 2014 version, is based on the sandbox principle. Potential malware is first executed in a sandbox to evaluate its behaviour. According to Avast, malware uses new technologies to escape from this kind of protection, but its engine is continuously updated together with definitions, so it always includes the latest control features to avoid being deceived with a clever trick.
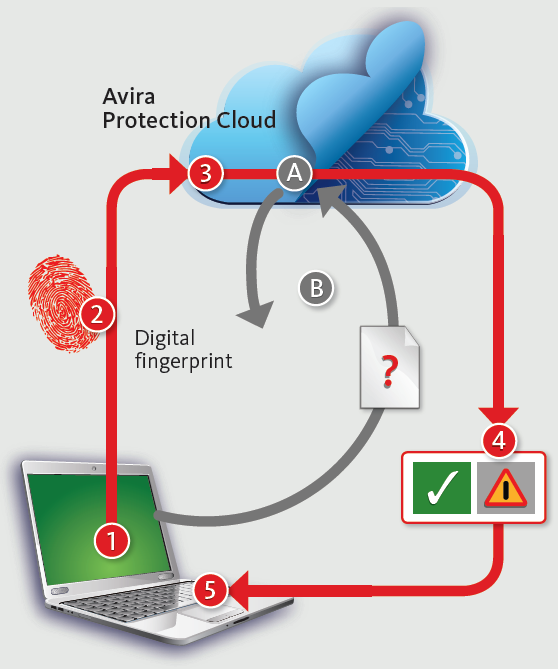
Avira recommends to activate the Cloud-based protection (Avira Protection Cloud -- see the image on the side). This technology sends a fingerprint of suspicious files to the laboratories of this famous security firms to check if it’s an already analyzed executable. If the file is not recognized it’s immediately uploaded online and analyzed. Avira leverages several techniques to overcome the anti-debugging and anti-sandboxing technologies implemented by malware.
Read more How to protect: technologies of the main antivirus and security producers
How to backup PCs/servers
In order to prevent ransomware to infect your backups you can’t store them on a regular network share or on an USB disk: you must choose a local, not accessible backup or a Cloud backup like 1Backup or a similar service.
In this issue of GURU advisor we’ll explain how to leverage snapshots of the ZFS file system with FreeNAS and be protected against ransomware.
The ideal scenario is where your backup is performed on a separate Nas or server which is not linked to any domain or has reduced privileges (principle of least privileges). In any case no clients in use should directly access backups without a password (which also must not be stored). If you are already using a backup software on clients, check if you can add a pre/post backup command to use to add and the disconnect shares immediately after use.
Read more Ransomware, how to protect: secure backups and specific tools to prevent infectionsLet’s return to one of the most dangerous and aggressive threats of the last years: ransomware, aka crypto-viruses: harmful software that encrypts or steals user data and asks for a ransom.
What is changing? How these viruses are evolving? Are there any reliable solution to get protected? It’s not easy to answer to all these questions, but a sysadmin, a technician or an IT manager today must know very well this topic and study all the possible strategies to protect data, be it on premises or outside the company.
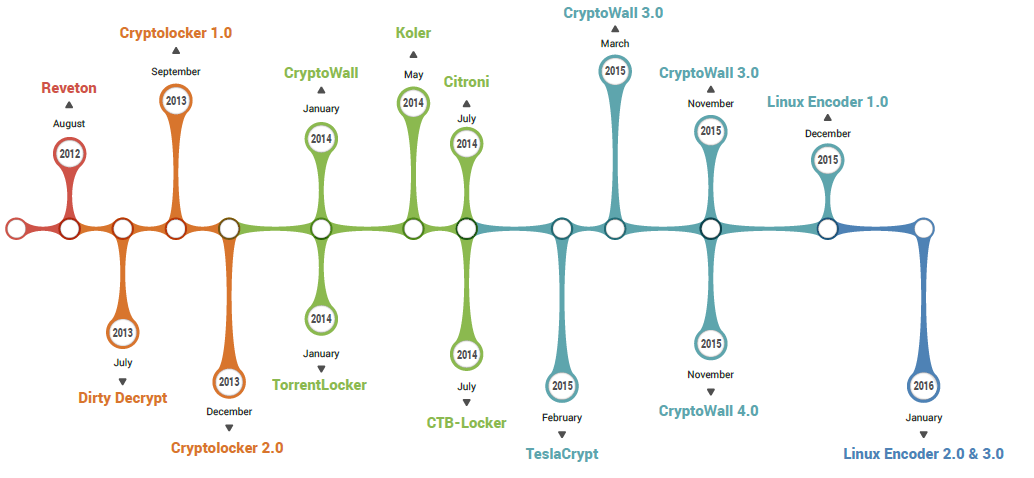
Read more Ransomware: how they are evolving - the latest news from Cryptolocker & Co.
No just new products, but also a prolonged and active support
Professor Kevin Curran from IEEE spoked about privacy, cookie law and ransomware.
During MWC we’ve met lots of people that work in a business environment and talked about their company’s vision. We had a pleasant chat with an IT professor, Kevin Curran from Ulster University in Northern Ireland, IEEE senior member, the important organization that takes care of the technological progress with a particular attention to the advantages and benefits that are brought to humanity.
How is your visit to the MWC going? what do you think about the innovations presented here?
There’s a lot of fuss about 5G as the evolution of 4G, despite 4G being not a standard yet. Everybody's talking about Cloud and Internet of Things. All these technologies are important and interesting, but in my opinion there's a lack of attention to standardization and to the support of products that are announced and brought to the market for mere economical reasons.
-
BYOD: your devices for your firm
The quick evolution of informatics and technologies, together with the crisis that mined financial mines, has brought to a tendency inversion: users that prefer to work with their own devices as they’re often more advanced and modern than those the companies would provide. Read More -
A switch for datacenters: Quanta LB4M
You don’t always have to invest thousands of euros to build an enterprise-level networking: here’s our test of the Quanta LB4M switch Read More -
Mobile World Congress in Barcelona
GURU advisor will be at the Mobile World Congress in Barcelona from February 22nd to 25th 2016!
MWC is one of the biggest conventions about the worldwide mobile market, we'll be present for the whole event and we'll keep you posted with news and previews from the congress.
Read More
- 1