- Details
-
Published: Monday, 09 November 2015 16:14
-
Written by Lorenzo Bedin
Viruses evolve along with technology, too: nowadays the goal of the hackers is exclusively to profit from IT crimes. In this scenario, ransomwares -malwares that ask for a ransom- are an explicative example of this trend.
There is no sysadmin that hasn’t already dealt, directly or not, with Cryptolocker, Cryptowall or one of their forks. These viruses quickly encrypt all the content of a computer with a secret key once it gets infected: to decypher the compromised data -when an updated backup, protected from the same virus, is not available- the only way is to pay a ransom.
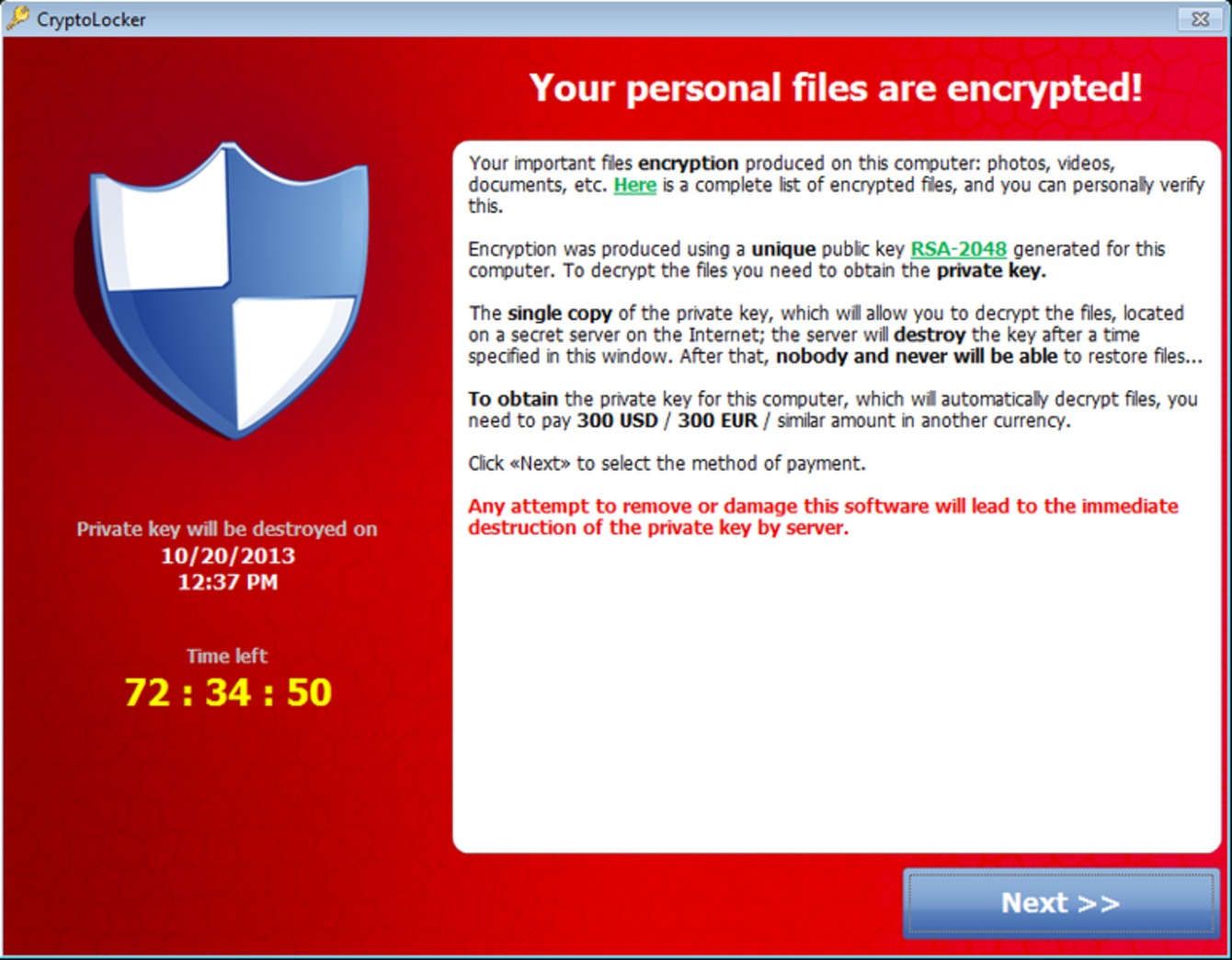
Here's a screenshot you might bump into after yout files have been encrypted by a Ransomware
Read more ...
- Details
-
Published: Tuesday, 03 November 2015 10:58
-
Written by Alessio Carta
Kerio Control is an integrated solution for perimetral control of the network that falls in the category of UTMs (Unified Threat Management). It’s a system capable of managing threats in a unified way with a single interface for the configuration of the various settings.
Kerio Control, version 8.6.2 at the moment we write these lines, is a stateful inspection firewall, an IPS/IDS system, a traffic balancement gateway, a DHCP server, a DNS forwarder, a Web content filtering system and a VPN server for secure connections with remote users. The list of the features found in Kerio Control is long, and you might want to consult it at the official Kerio site here: http://www.kerio.com/products/kerio-control/features.
Read more ...
- Details
-
Published: Monday, 26 October 2015 10:39
-
Written by Filippo Moriggia

F5 Networks has a modern platform that unfortunately isn’t widely known; we have talked with Paul Pindell, Senior Solution Architect at VMworld 2015.
Let’s start with the offer of F5 Networks and try to better understand what you do
F5 Networks offer a full proxy architecture that allows to analyze all the traffic that enters and goes out the business walls and its branches. Traffic gets analyzed and decrypted even if chypred standards, like SSL, are used. Out technologies then operate on the whole traffic to perform several functions such as firewall, routing, security management on the application level, acceleration and compression and even a Web content control. The strength of F5 is in the intelligence that allows to manage this architecture.
Read more ...
- Details
-
Published: Monday, 26 October 2015 10:19
-
Written by Filippo Moriggia

During VMworld we ad the chance of meeting Jason Bandouveres, Director and Product Management for Fortinet’s virtualized solutions.
What do you think about the presence of Fortinet here at WMworld and the position of your company with regards to the evolutions of the threats for security?
Fortinet is a company with 15 years of experience in the network and system protection field, and it’s ready to face all the novelties that the Software Defined systems are bringing. Fortigate, out most known and used product, is one of the most complete UTM (Unified Threat Management) and has some fundamental features, like an Operative System that has been developed internally and profoundly optimized (FortiOS), an internally developed antivirus engine and a system dedicated to the protection against 0-day threats.
Read more ...