- Details
-
Published: Tuesday, 11 October 2016 20:18
-
Written by Filippo Moriggia
Here’s 7 simple rules to follow in order to guarantee integrity of data, never forgetting good sense.
Actually, it’s like convincing someone of the usefulness of warm water - every professional of company should always have an updated and complete backup that provides an easy restore - yet unfortunately every time I talk with an IT responsible, consultant or sysadmin I discover, with my great surprise, that some basic concepts are misunderstood or ???, if not even unused.
Let’s list the 7 requisites of a good backup system.
1: “2 is better than 1”: an additional copy isn’t a pity
Don’t ever think that a single copy on an external HD, NAS or resource is enough. Failures are always around the corner and you’ll get to face them in the worst moments. Therefore duplicate your backups on two different supports at least, even if the main one seems to be adequately reliable. You don’t have to copy everything: if you make, say, a complete backup of each computer, probably copying terabytes of data is a waste. Backing up critical data (ie documents and emails) however must be done on (at least) two different supports, both of them reliable.
Read more ...
- Details
-
Published: Friday, 30 September 2016 10:59
-
Written by Lorenzo Bedin
There are tens of different software and services that allows to hold a meeting, a conference or a webinar, however it’s not easy to understand what is the product that fulfills your needs. So we have selected and tried the most interesting and complete software of this sector for you.
The two terms we’ve just used (meetings and webinars) both describe, albeit with little differences, the two main situations where such software are implied. In the first case it’s essentially an easy and handy method to make an online meeting by sharing the screen, files or images. The number of participants is usually limited and interaction is high: for instance, anyone can take control of the presentation and everybody can talk at the same time.
Conversely, in the case of webinars (a portmanteau between the word Web and seminar) the number of participants can be very high, even hundreds, while the level of interaction lowers as usually the speakers are a limited group of people.
The use of these technologies brings advantages in logistical terms and cost-reduction as it can cancel geographical distances with the aim of a computer or a portable device like a smartphone or a tablet.
Types of infrastructures and supported platforms
The vast majority of software we have tried is sold as a service, with a monthly price calculated usually on the number of participants. Only a few software are sold with a license (that is paid once). Some applications like WebEx by Cisco offer an as-a-Service version and an on-premises version, called WebEx meeting Server). The same holds for ScreenConnect by Connectwise, which is a product aimed to remote control but also includes some specific features for online meetings (we have covered it in the previous article on MSP platforms).
Read more ...
- Details
-
Published: Monday, 08 August 2016 12:21
-
Written by Riccardo Gallazzi
An essential tool found in the toolbox of every Service Provider is remote control software, a type of software that allows to execute commands and actions on a computer situated in another place, leveraging an Internet connection. Let’s see what are the characteristics of a good remote control software, also introducing some of the available solutions.
The architecture
All remote control solutions we cover in this article are based on an architecture that calls for a host, a gateway and a client (also called guest). The host is the computer to be controlled, on which we can install an agent that sets the remote connection while being executed as service (in Windows) in order to let it run as soon as the operating system is loaded.
The client is the local computer where we can run a specific software, called viewer, which can visualize the remote screen and we use to perform operations.
If both host and client are on the same subnet, on a VPN if needed, visibility is direct and there aren’t any issue in terms of configuration and security (save for the overall network security), but if both computers are on different networks, then some problems arise as there are NAT systems to overcome and it’s mandatory to leverage at least a secure authentication and traffic encryption system for the sake of security.
In order to overcome the obstacle, a third element is introduced in the architecture: a gateway server which abstracts the connection between host and client. Such server is provided by the software produces and guarantees the proper security of connections. Solutions belonging to this review all adopt a combination of public/private key authentication and data encryption. In this way Man in the Middle (MiM) attacks are avoided and intercepted data are unusable thanks to encryption.
Read more ...
- Details
-
Published: Monday, 08 August 2016 11:16
-
Written by Lorenzo Bedin
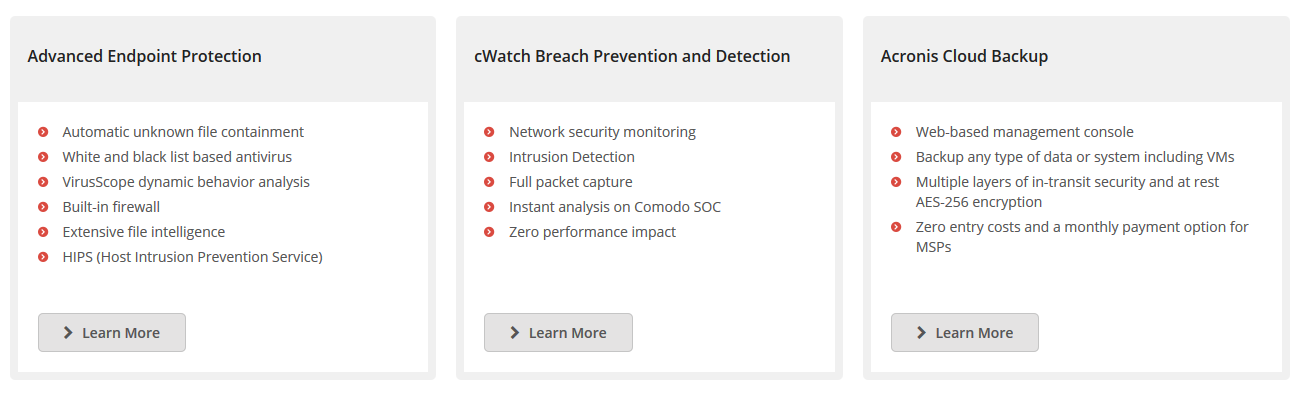
In the last issue we’ve talked about useful tools for those who want to be Managed Service Providers (MSP) and covered a number of platforms for the management (both technical and administrative) of the clients’ infrastructures. One of them is Comodo One MSP, which the colossus of IT security Comodo makes available for free (with some limitations that can be avoided with the Premium plan).
The free access to the product is the strength point for sure of the Comodo One MSP platform (One onwards), which integrates the three main features every MSP needs: Remote and Security Management, Path Management and Service Desk with Ticketing capabilities. Remote and Security Management and Patch Management belongs to the family of RMM (Remote Monitoring and Management) products that are used to maintain control of the infrastructure and perform maintenance actions for clients. Remote control, resource monitoring, automated notification and management of upgrades are part of it.
Service Desk with ticketing, time tracking and documentation capabilities is more part of the PSA (Professional Service Automation) world.
For those who want more than the basic features, several upgrades are available (some are free, some are paid) allowing higher levels of protection and additional modules. For instance, there’s a better endpoint protection with an advanced firewall and Host Intrusion Prevention, and the package dedicated to network security offers better monitoring and intrusion detection capabilities, and a system for the capture and analysis of in transit packages. Among the upgrade we can also find the Acronis client for Cloud backup (Acronis Cloud Backup).
Other available modules are Antispam Gateway, Dome Shield, Korugan Central Manager (RMM category), Comodo CRM and Comodo Quote Manager (PSA category). Note how some of these additional modules are free (like Quote Manager, the package used to prepare quotes), and other can be installed for free but with a basic configuration (like cWatch Basic, a component for network security). In each case, after accessing to the specs of each one, you can find information about prices.
Read more ...
- Details
-
Published: Wednesday, 29 June 2016 18:12
-
Written by Lorenzo Bedin
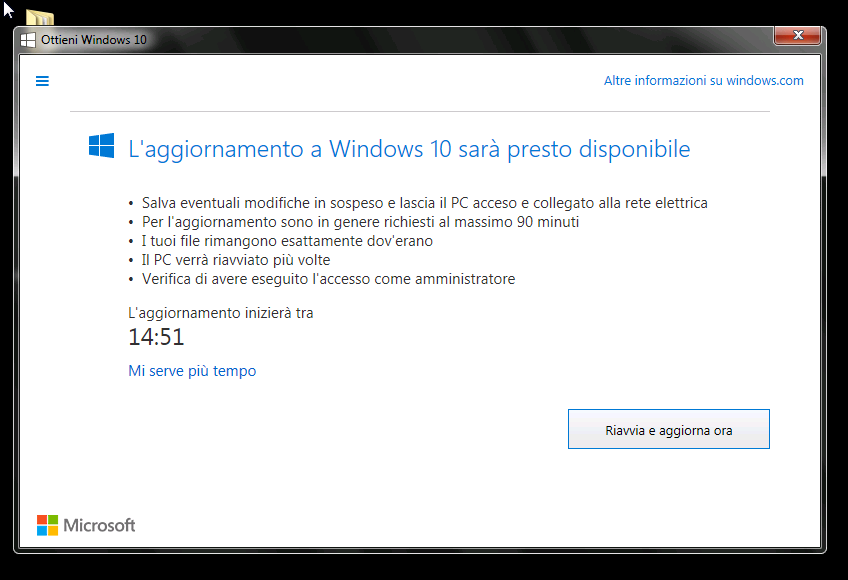
The release of a new operating system is an usual scenario for IT pros. The release of Windows 10 is no exception to that, but the way of distribution experimented by Microsoft has certainly changed.
For the first time in the history of the OS from Redmond, users of the previous of Windows (7, 8 and 8.1) can download and install for free the upgrade to Windows 10, naturally maintaining an equivalent version to the one previously installed (ie. 7 Professional becomes 10 Pro) and related license. However the insistent distribution method has beared a certain dissatisfaction amongst users and professionals. This feeling is also emphasized by the integration of the Windows 10 update straight into Windows Update (which results in an automated installation in most cases) and by the pounding notification campaigns for non-updated computers.
Read more ...
- Details
-
Published: Wednesday, 29 June 2016 18:06
-
Written by Lorenzo Bedin
The term MSP is the acronym for Managed Service Provider and identifies a working method nowadays used by many companies in the IT world. In general, the idea of Managed Service implies an outsourcing approach of management and maintenance activities with the ultimate goal of optimizing the use of resources and lowering costs of the client. In this scenario, the Provider is the company or society that provides the service.
MSP key points
We can define three main points that characterize a Managed Service Provider (MSP onwards):
- unlimited phone/remote help desk;
- proactive management of the infrastructure: backup, security, updates, etc..;
- being a competent intermediary with additional providers and third parties.

Advantages and rates
Essentially a MSP contract is an “all-inclusive” contract with reciprocal advantages for both the provider and the client. In this way the client can have a fixed price for IT management, without worrying about any technical aspect or surprise about costs. Moreover, the client is aware the goal of the provide is the same of his own, ie to reduce down times and increase the overall productivity of the company.
Read more ...
- Details
-
Published: Monday, 23 May 2016 17:52
-
Written by Riccardo Gallazzi
The quick resolution of problems is a fundamental activity for any sysadmin. Let’s discover some tricks and advices to become better and faster at diagnosing and resolving troubles of a Linux system.
In the last issues of GURU advisor we dedicated an article to those commands suitable for a basic Linux troubleshooting in a VPS context, but when top, ps and netstat are not enough, we must aim to more advanced tools. Troubleshooting is an activity that can easily transform into a waste of time and resources, proportional to the difficulties of the problems to be solved. In order to optimize the results and limit unuseful trials and tests it’s mandatory to act following well-structured procedures.

The USE method -which stands for Utilization, Saturation and Errors- was originally conceived by Brendan Gregg (who wrote an omniscient book on the topic: Systems Performance - Prentice Hall, 2013) and has its basis in a simple and efficient idea: defining a workflows that determines the level of utilization, saturation and possible errors for each available resource. In this way we can gradually reduce the number of possible causes of the misbehaviour until we can precisely identify the cause of the loss of performance.
Defining resources is quite easy: they are the physical components of a machine (we can apply the method to software components, but it would get very complicated and detailed -- perhaps a bit too overkill given the scenario), a server in our case -and the equivalent virtual version. Processor, memory, disk, controllers, network interfaces, buses, etc..
Naturally the better the knowledge of the architecture, and the faster and more precise the results will be, albeit implying a certain complexity and a steep learning curve.
Read more ...
- Details
-
Published: Monday, 23 May 2016 00:00
-
Written by Filippo Moriggia
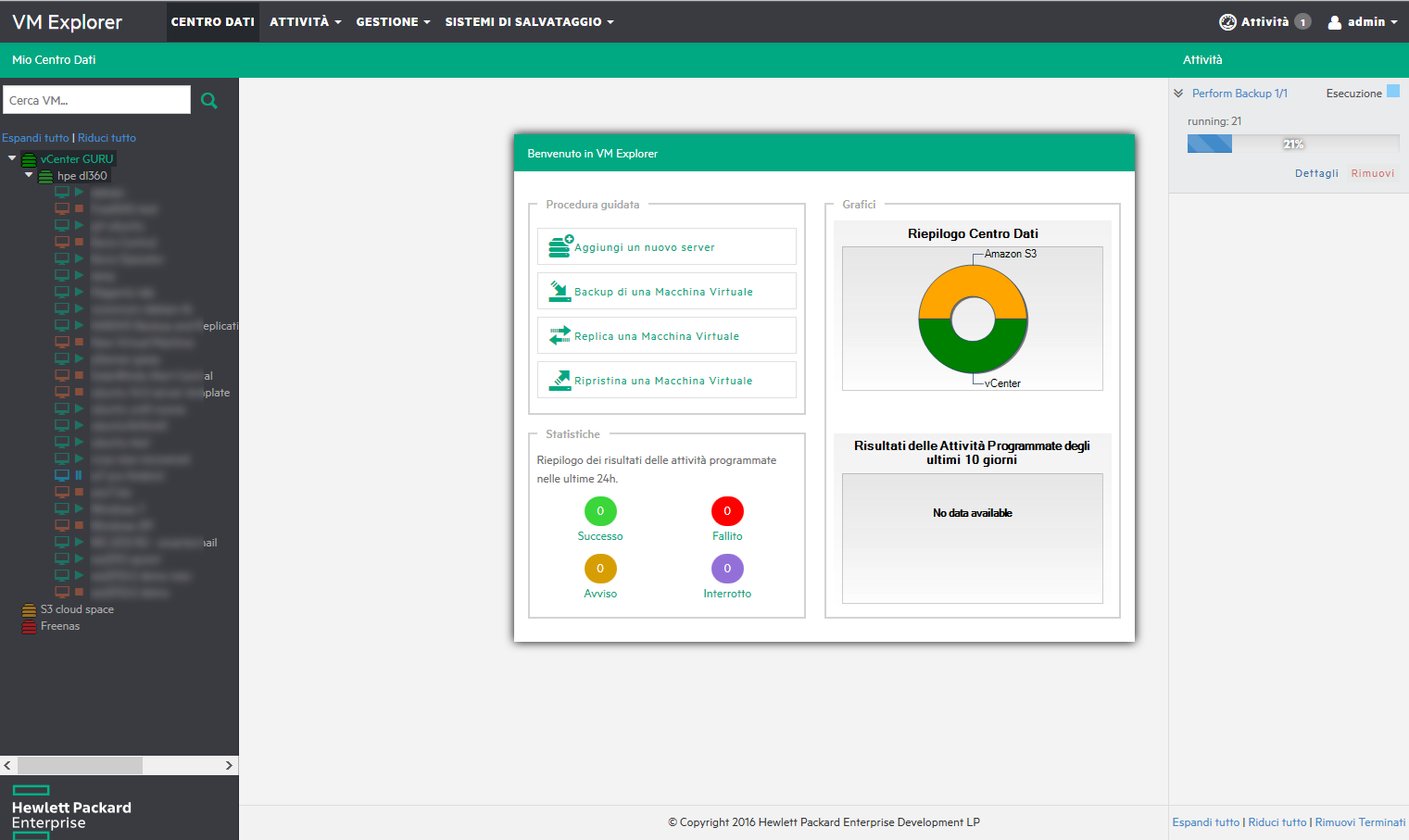
VM Explorer is a software that has been developing by the Swiss Trilead since 2007 and count more than 10.000 worldwide clients. This number is going to increase, mostly considering the growing authority gained after the recent acquisition by HPE, as Roberto Beneduci of CoreTech, the historic distributor of the brand in Italy, confirmed: “With respect of the same period in 2015, in the first three months of 2016, the number of VM Explorer licenses sold has more than doubled.”
A well justified acquisition
HPE already had an Enterprise tier backup software, the HPE Data Protector Suite and has, with its server, 60% of the VMware OEM market. With VM Explorer HPE can offer its clients an easy, robust and cheap solution, uniquely dedicated to the backup of virtual systems, very different from Data Protector, which is a solution addressed to a different client tier (infrastructures with thousands of VMs). With this move HPE can now offer all its clients of the Small and Medium Business tier (<100 VMs) a less complicated offer and, under certain aspects, more appealing that the widespread solution by Veeam.
Read more ...
- Details
-
Published: Friday, 20 May 2016 18:32
-
Written by Lorenzo Bedin
With a coup de théâtre like in a spy movie, the developers behind the feared TeslaCrypt ransomware finally decided to end its development and diffusion project and openly published an universal key to decrypt files.
In an article on last month’s issue we dealt with the ransomware phenomenon: TeslaCrypt is for sure one of the most feared and widespread virus of this kind. Luckily, we have a good news: an universal decryption key is available and ready to be used by those who have been infected by this virus.
A researcher of Eset -the renown software house that develops the Eset antivirus- contacted the developers of TeslaCrypt with the support chat of the ransom payment portal and, pretending to be an user hit by the ransomware, asked for a decryption key. With his uttermost surprise, he was delivered with the universal alphanumeric decryption key. Naturally a proper tool is needed in order to use such key, and this problem has been solved too: the developer BloodDolly, who released months ago his TeslaDecoder tool to decrypt files hit by the first versions of TeslaCrypt (1.0 and 2.0), updated his tool so it can now decrypt files created by versions 3.0 and 4.0 of the dangerous ransomware (the ones with extensions .xxx, .ttt, .micro, .mp3 or even without any extension at all).
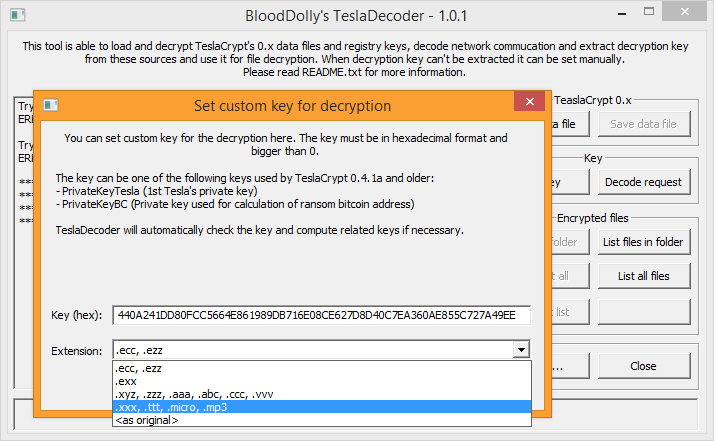
Read more ...
- Details
-
Published: Friday, 20 May 2016 17:50
-
Written by Lorenzo Bedin
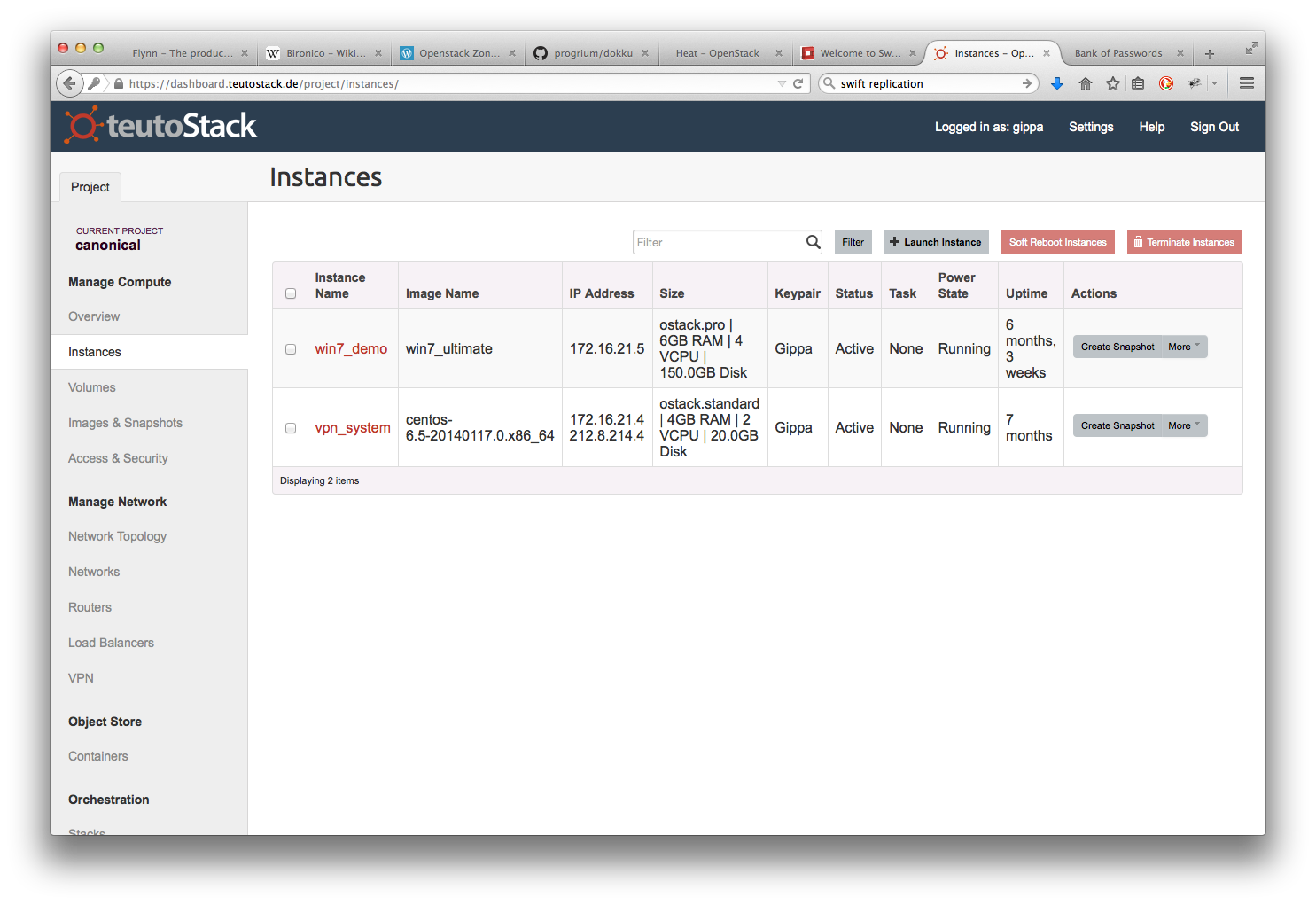
Pritunl is an open source platform capable of realizing distributed VPN networks. By leveraging the OpenVPN protocol it allows -according to the chosen licensing model- to setup virtual network architectures. In practice, it allows to easily connect devices inside or outside the walls, also in companies with two or more branches, creating a VPN managed with advanced rules and a centralized authentication system.Pritunl integrates several services of third parties like Amazon AWS VPC (Virtual Private Cloud, it’s a virtual network space in the Cloud available to users within the AWS suite) with automated failover and Single Sign On (SSO) authentication. Integration for the use of SSO include services like Google Apps, Slack, OneLogin Okta, DUO and Radius: each one of these service can be used to guarantee users the access to the Pritunl infrastructure with their own accounts and without having to use dedicated credentials. In case the Enterprise license is chosen, which allows the installation on an unlimited number of Pritunl server, the high availability with automated failover feature can be leveraged, also given the fact that there are no master nodes, instead each node acts as the same functional level of the others. Pritunl also integrates a server replication feature, thus offering an high level of scalability for clusters. With the aim of geographically distributed installations, the platform is based on the renowned MongoDB which offers an high level of reliability (in particular as the number of nodes and users grows) associated with the chance of replication.
Read more ...
- Details
-
Published: Monday, 18 April 2016 16:19
-
Written by Lorenzo Bedin
We’ve tried the Virtual Desktop Infrastructure (VDI) as-a-Service system offered by the American colossus. A few clicks of the mouse are needed to create and distribute virtual desktops that are complete and accessible anywhere.
VDI systems are'n any news in the IT scenario, just think about Citrix XenApp or less know but quickly evolving systems such as VMware Horizon. The real difference in terms of performances and availability, in particular for SMB, can be experienced only by switching to a Cloud-based solution. Choosing a Cloud Provider with an “as-a-Service” approach means not having to deal with any hardware and software infrastructure anymore: the only requirements are an Internet access and whichever terminal, a tablet or even an old PC with Linux or an employee’s laptop -that’s a BYOD logic- and you’ll be ready to offer an updated, complete and always available business desktop.
It’s worth to point out two main limits in the adoption of these solutions: one is about software, the other’s about hardware. The former implies software licenses management: Microsoft has never been friendly in terms of VDI solutions and probably it’s easier to find systems where licensing has been interpreted or configured in a wrong way, even though all the other things have been properly done.
The second limitation is about guaranteeing good performances to users’ desktops in every situation: it’s not an easy task to implement a system (hardware, software, hypervisor and so forth) that can provide enough resources in every situation, in particular for small System Integrators or less experienced Cloud Providers.
Read more ...
- Details
-
Published: Monday, 18 April 2016 15:11
-
Written by Lorenzo Bedin
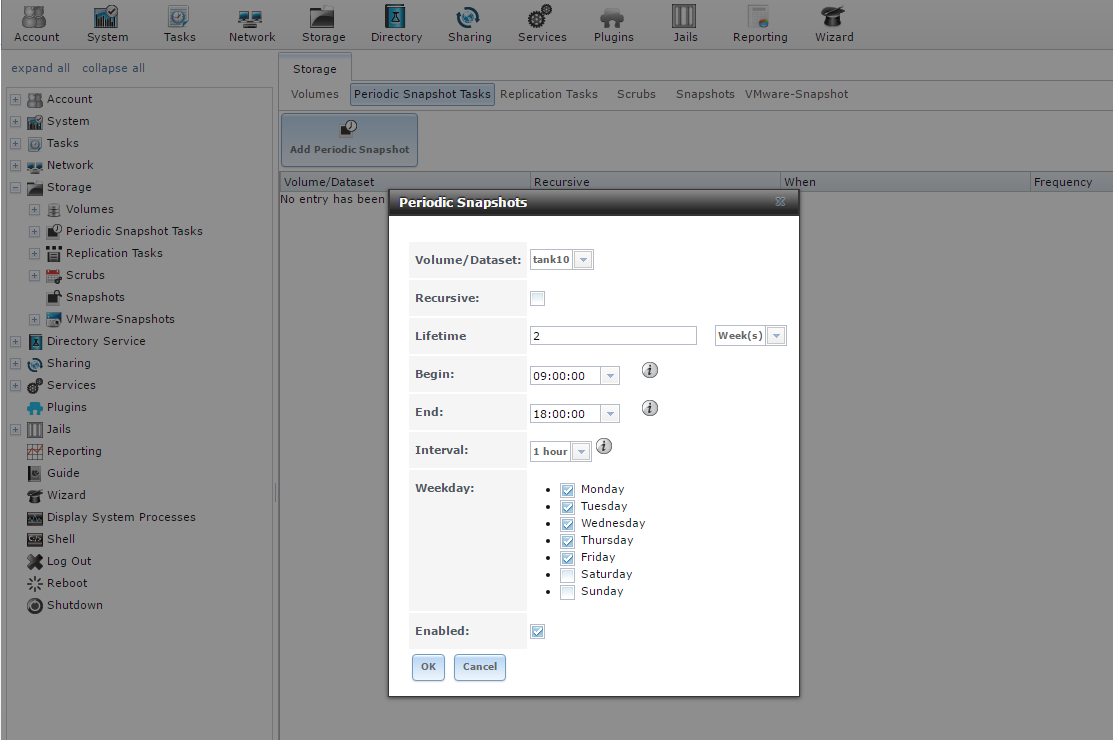
We’ve already talked in deep about the features and the advantages of FreeNAS as storage resource: in this article we focus on how to create, use and restore snapshots in a very easy and practical ways.
A snapshot can be described as a “photography” of the storage state in a certain point in time that allows the so called “roll-back” to a previous situation. Thanks to the Copy-on-Write method of ZFS, described in the a previous article, snapshot operations are quick and take a few space. Starting from a functioning FreeNAS installation with a configured storage, the most common situation we encounter is a ZFS volume which is mapped to one or more shared network folders. Such shares can be attacked by a ransomware or can be simply accidentally or partially deleted. In a situation like this, the presence of properly configured snapshots can be a life-saving solution.
Read more ...
- Details
-
Published: Thursday, 11 February 2016 13:13
-
Written by Filippo Moriggia
What are the IT needs of most small Italian businesses? A reliable email server offering functional and ample mailboxes, one or more on-premises shares to share files and backups, a firewall/gateway for external connections with VPNs, a good level of protection against viruses, a backup system (online too) and basic collaboration tools for the employees.
Sure this brief introduction brought to your minds many software and appliances capable of satisfying one or more of these needs, but you’ll probably experience some difficulties in finding a single product that does all of that. ClearOS is an Open Source project based on Linux that offers almost all of these features and can be managed by a well organized, functional and handy Web interface without using a command line. Even if it’s an Open Source project, fortunately ClearOS has a company behind it (ClearCenter) that is not limited in the development and updating process, but also offers a wide marketplace with maintenance services, antivirus updates and additional features available exclusively through commercial packages.
Read more ...
- Details
-
Published: Friday, 05 February 2016 17:06
-
Written by Lorenzo Bedin
FreeNAS is a FreeBSD-based Operating System whose development began in 2005 thanks to Olivier Cochard-Labbè and whose main function is to transform the computer or server where it’s installed in a NAS (Network Attached Storage). The system was conceived to require a limited use of hardware resource, apart from storage, so that it can run smoothly also on old or performance-wise limited machines.
The development of FreeNAS went on with the years and reached the actual 9.3 stable version and 10 “Alpha” version (the support to the 32-bit UFS file system was abandoned in 2014). In 2009 iXsystems (a company dealing with servers and storage solutions) showed interest in the FreeNAS project in order to avoid the migration of the system on Debian and the subsequent loss to the support for ZFS, after the then project leader. After an important revision and update by the iXsystems’ team, in May 2011 FreeNAS 8.0 was released.
FreeNAS is based on the OpenZFS implementation of the Sun (then Oracle) system called ZFS, so it takes advantage of all the code base of this project to manage ZFS volumes, disks and devices.
Read more ...
- Details
-
Published: Monday, 18 January 2016 18:57
-
Written by Filippo Moriggia
Backup & Replication allows to protect VMware infrastructures, it integrates with Amazon and vCloud and is ready for multi-tenancy

The most innovative backup and disaster recovery solutions of the last years are all related to the virtual sphere, also because nowadays the use of hypervisor is implied in the construction of whatever server infrastructure or server. Nakivo is certainly one of the youngest players in this sector and only offers -at the moment- a backup solution for the VMware platform, but in the last few years it has showed a dramatic growth in terms of available features.
We tried version 5.9 that goes well beyond the idea of simple backup of virtual machines, and offers a quite sophisticated infrastructure based on distinctive elements that can integrate on the local network or to connect different offices, branches or datacenters.
These elements are Director, Transporter and Backup Repository; they can talk amongst them also from distinct geographical positions.
Flexible installation
Nakivo Backup offer the best flexibility in terms of installation: indeed it’s available as Windows or Linux installer, but it can be deployed also as a virtual appliance. In this case the choice is vast: the Full Solution appliance is suitable for smaller installations and offers all the elements of the architecture, while bigger and more demanding installations can leverage single components or a combination of them. The Director is also available in a multi-tenant version for those who provide Backup, Recovery or Disaster Recovery services to different clients.
Nakivo offers a complete scheduling of backup jobs
There are several advanced options available
Tenant configuration is immeadiate using the dedicated panel
You can manage several accounts from the dedicated dashboard
The dashboard shows the main information of backups status
Data traffic monitoring is available as well
You can also monitor the status of the storage devices used as repository
Appliances, which can be installed in a few minutes using the OVF deployment procedure in vSphere, are based on Ubuntu Linux and, by default, have 4 Gbyte of RAM, 2 vCPU and the disk takes a couple of Gbyte if configured in thin mode (almost 550 Gbyte if thick mode, 30 are for Director Multitenant). Nakivo’s official requirements ask of at least 4 Gbyte or RAM for Director and Transporter and 350 Mbyte for each additional job to execute simultaneously. Talking about operating systems, Nakivo Backup & Replication supports Windows Server 2008 R2, 2012 and 2012 R2 in addition to Windows 7 Professional and 8 Pro. Supported Linux platforms are Ubuntu 12.04 Server, Suse Linux Enterprise Server 11 SP3 and Red Hat Enterprise Linux 6.3..
Nakivo Backup & Replication also allow to retrieve single files inside VMs: supported file systems are Ntfs and Fat32 for Windows machines, Ntfs, Fat32, Ext3, Ext4 and Xfs for Linux machines. You can also restore single objects in Microsoft Exchange (versions 2007 and 2010) and Microsoft Active Directory (on Windows 2008, 2008 R2, 2012, 2012 R2).
A software for everybody
Despite the complexities at the basis of Nakivo naturally grew with the growth of its features, the product still remains one of the easiest to use on the market. The interface of the program is accessible via Web at the IP address assigned to the VM (port 4443, HTTPS of course).
The initial configuration procedure can set the vSphere server (or servers) to protect indicating the vCenter credentials, decide whether to use the integrated or an external transporter and specifically defined repositories to store backups.
Once completed this step you can create the first jobs, or switch to the advanced configuration to complete the system configuration. It’s a good habit to set the SMTP server to send reports, for instance: server with SSL certs with or without authentication are supported, and different email addresses can be set to send report abouts jobs, error or warnings and an overview report.
In the global configuration section you can modify the Web interface with a custom logo and background: resellers that want to offer the product with their brand can easily do that, they can also change the support email address and the name of the company. From the same section you can access to the Licensing management and to an useful Events section with the log of all the systems event, from complete backups to modified parameters.
Backup or Replication
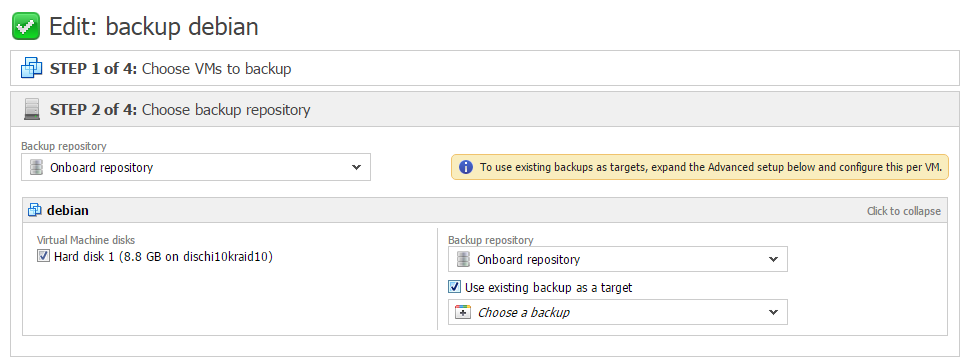
Nakivo allows to create backup and replication jobs. The first step in the creation of a backup is to select the VM (or the VMs) to save, then select the backup repository: obviously the available ones are the ones defined according to the configuration of the program. If some backups are already present on the selected repository, you can choose whether to use the existing archive as destination or to create a new one. The third step is scheduling the time and the frequency of the backup, while the advanced options are specified in the final phase.
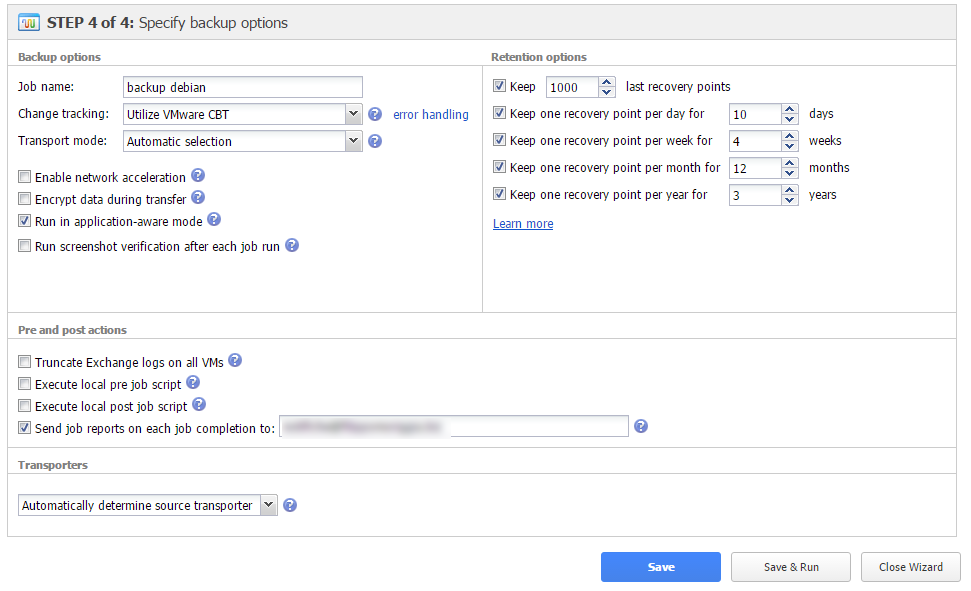
To identify modifications, Nakivo leverages VMware’s CBT (Changed Block Tracking) technologies or its own. VMware’ technology is the default and suggested one, but in the job it’s possible to define a behaviour to adopt if vSphere notices an error: the proprietary solution is a possible choice, alternatively a reset of the CBT configuration can be tried, or simply let the backup fail. In case of error you can also enable the “Double check changed blocks provided by CBT” option that performs a double check in order to prevent CBT from creating backups with an exaggerate dimension due to some problem. The technology by Nakivo to check changed blocks is used even if the VM is powered off: in this case VMware CBT is not available.
If the backup destination is not local, you can enable the network acceleration feature so that you can save traffic by using data compression and reducing the needed bandwidth. In these cases it’s useful to enable ciphering during transfers.
On Windows VMs that are being backed up, you can enable the application-aware mode that leverages VMware’s quiescing systems (based, on its turn, on Microsoft’s VSS) in order to avoid suspended writings, thus guaranteeing a consistent backup even if the operating system is still running.
Automated backups check
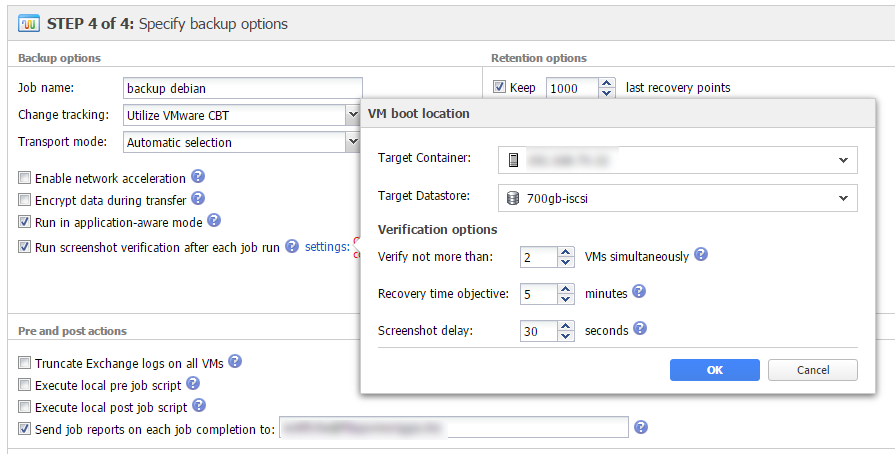
Nakivo Backup can automatically test backups immediately after the execution and provide as “evidence” of the test a screenshot of the restored VM. You just check the Run screenshot verification flag and compile the form that appears after the selection is active to define the test environment parameters: hosts or clusters and datastores on which perform it and number of VMs to test together, wait time before screenshot and RTO (Recovery Time Objective), that is, greatest time needed to restore that can be considered sufficient in order to talk about efficient restore.
Data retention options
As all backup softwares, Nakivo too allows to define a number of recovery points that establish the data retention level. You can keep only the last -nth recovery points and at least a point for each number of days, week, months and years defined in the options.
Repository backups of Nakivo store restore points in a single central archive, organized according to jobs, VMs and date.
Nakivo Backup & Replication can also run scripts before and after backups: it supports Windows scripts (if using a Windows VM) and Linux scripts (only if run in a Linux environment). It cans also wait until the end of scripts in the starting phase and mark the job as failed or successful according to the status of the script. If the machine to backup has Exchange running, Nakivo can truncate the logs of the Microsoft application to limit the dimension of the VM after the backup has been successful. Obviously, it requires a Windows user with administrative permissions.
Always ready replication
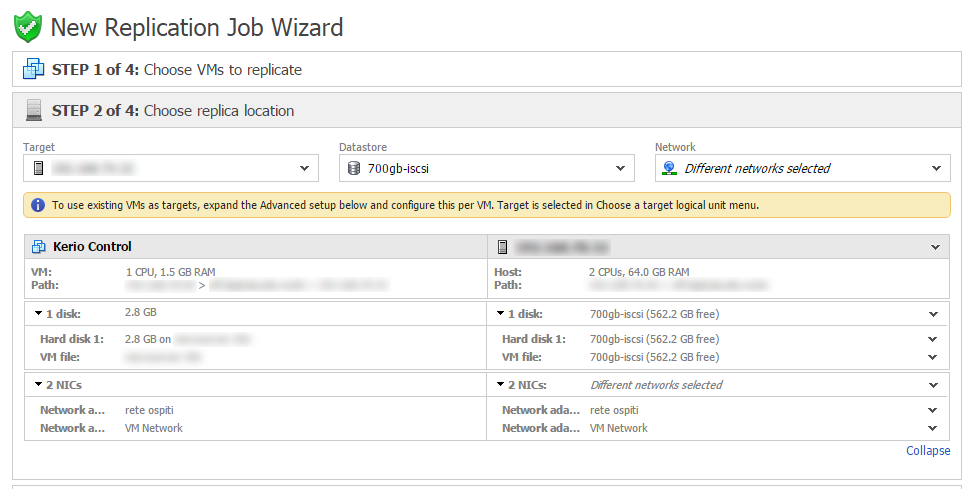
The procedure to create a replication is similar to a backup one: the main difference is, obviously, the choice of the destination. You don’t need to select just a repository, instead you need to specify the destination host or cluster for replication and the datastore and network configuration for the VM to be created. Replication too can be scheduled to be executed at certain times, and the same considerations about Block Tracking technologies, recovery points and screenshot verification still hold, as we’ve talked about backups. Among the specific options it’s worth to note you can use a different name for the created VM (for instance, appending “-replica” to the original name) and enable the use of only Thin disks.
Repository: internal or external
Nakivo Backup supports two kinds of backup repository: Windows network shares (based on CIFS, therefore compatible with Linux or dedicated NAS) and its proprietary repository based on a machine or an appliance with Transporter installed. Naturally the storage of such VMs can be then placed on any datastore supported by VMware.
The max limit of available space on a Nakivo repository is 128 Tbyte: the software itself compresses and deduplicates VMs on a block level. Data is then natively stored in terms of incremental data with respect to the first, complete backup: you don’t need a periodic “full” backup. Deduplication is enabled by default but is can be disabled should you use a storage that automatically deduplicates data. Storing backup on tapes is supported, but this operation must be performed with third-party software or with a simple script-based copy: the repository however must be “detached” in the copy towards tape by Nakivo using the scheduled linking and unlinking capabilities available.
Independent NAS
A completely innovative feature introduced with Nakivo 5.9 is the chance of using the software itself inside a compatible NAS. This allows to make the backup procedures completely autonomous and independent from the main VMware infrastructure, thus saving precious VMware host resources. Naturally not every NAS is supported, but the list is ever growing and includes more than 20 different products by Synology and 2 models by Western Digital. The software can be easily uploaded using the Windows and Linux installer made available by Nakivo and it allows to leverage supported NAS as a complete backup solution that cover all the elements of an infrastructure. Nakivo can, indeed, run on a quite low-end NAS, as it requires just 2 cores (Intel CPU) and 1 Gbyte of RAM to work properly.
Easy recovery in the Cloud
Amongst the most advanced available features there’s the direct integration with the Amazon Web Services (AWS) and vCloud director cloud. You can enter, in the configuration section, the credentials of AWS and define the region and initial space to allocate. This way you can directly take advantage of the EBS (Elastic Block Cloud) space to store backups and replications, and be ready to restore a VM in Amazon’s cloud.
Backup in Amazon S3 (Simple Storage Service) is not supported at the moment, while you can use a service like vCloud Director setting the remote server in the Inventory of Nakivo Backup & Replication.
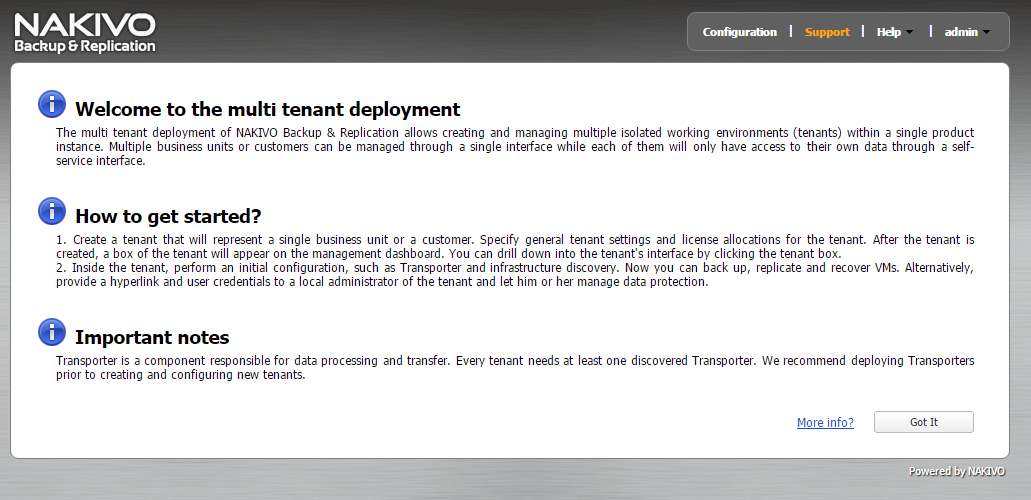
Ready to be multi-tenant
Those who have a cloud infrastructure, or even a small datacenter, and wants to provide backup service for clients will find in Nakivo a system easy to configure and capable of running with limited resources. The Director appliance for multi-tenant solutions indeed allows to create completely distinct environments for each client by directly associating licences for each of them, starting from at least one socket. The selection of host, backup repository and Transporter is set by the system administrator and can be hidden to single clients: each client can create and administer his/her own backups, replications and restore procedure if he/she is an administrative user. If needed, guest credentials can be created to see reports and dashboard and, optionally, restore files and objects from Exchange or Active Directory.
Licensing for everybody
Nakivo is sold in 4 different versions: the first one and cheapest (169 $ per socket, VAT excluded) is Pro Essentials, available in packages for 2, 4 and 6 sockets; it includes the backup and replication capabilities, including restore on Amazon, restore files and objects from Exchange and Active Directory. The only things missing are the Multi-tenancy features, Branding and License delegation and the local administration of remote branches. The Enterprise Essentials version (249€/socket) maintains only the purchase constraint of 2, 4 or 6 sockets packages, while the Pro (329€/socket) and Enterprise (509€/socket) have the features of the relative Essentials versions, but they can be also sold starting from a single socket, without any limitation, not even upper limits.
Conclusions
Nakivo Backup & Replication performed very well in our tests, proving to be reliable and quick, both as an integrated solution and using the separate architecture with Director, Transporter and Repository. The software is easy to manage and configure, the documentation (available in English language) is complete and easy to consult. Who would like a documentation in Italian can look at Avangate Italia (Nakivo Gold Partner), which also organizes Webinars periodically (like this one) to explain features.
We haven’t experienced any difficulties at all even in the most complex operations, like preparing a multi-tenant architecture: the use of the Web interface then allows you to easily interact with the system even if being out of the office or doing a remote intervention for a client.
Reporting features are good too, and we appreciated the notification messages via email that are clear and handy to keep under control the situation also when clients are many and infrastructures heterogeneous.
While not being one of the most complete solutions -in terms of features- available on the market yet, Nakivo Backup & Replication has a flexible and cheap licensing, thus making extremely interesting in an SMB sphere, where a light product, easy to configure and quite cheap guarantees a good level of protection even when resources are limited.
- Details
-
Published: Monday, 18 January 2016 18:07
-
Written by Roberto Beneduci
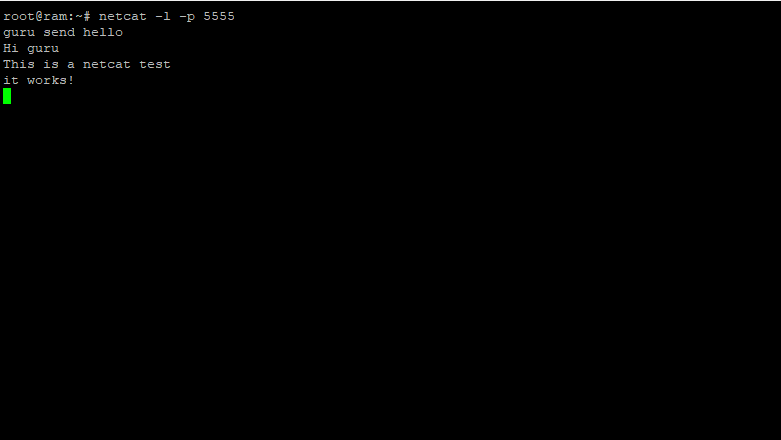
We’d like, with this article, to talk about some basic commands in Windows that are useful to perform diagnosis and network troubleshooting. These few commands, if properly used, allow to quickly come to useful conclusions and resolve the majority of the network troubles that are commonly encountered.
Quite often we get upset because a service or an application isn’t responding, we don’t remain focused enough to follow the required steps about network troubleshooting.
Let’s see how to behave rationally.
Read more ...
- Details
-
Published: Monday, 14 December 2015 17:58
-
Written by Lorenzo Bedin
Here’s SecurePass, a cloud-based service for multi-platform authentication based on One Time Passwords.

Password management inside a company is always one of the most delicated and debated topics, and it gets even worse as the number of employees and services to be managed grows. GARL, a Swiss company specialized in security systems, offers SecurePass, a centralized service for identity management.
This offer is composed of four different types of subscriptions that differ in the features included and, of course, the price. The entry-level offer (Personal) is free but has a maximum number of two users and only SSO authentication; as price increases, we have the Business, Enterprise+ and Service Provider plans; the details of the number of users included and the authentication modes supported are available at this link. We’d like to point out that all the prices are quite cheap (3 or 7 € at month per user).
Read more ...
- Details
-
Published: Monday, 14 December 2015 17:38
-
Written by Lino Telera
The evolution towards cloud solutions is one of the biggest revolutions in the IT sphere and it is completely changing the way of planning and evaluating infrastructures in a business setting.
It’s not a piece of news that the Infrastructure as a Service (Iaas) architectures allow system administrators to leverage the service model to consolidate servers, increase the availability of business applications and, in most cases, even to lower costs.
In the transition from virtualization to cloud, VMware has been one of the reference players for sure thanks to its advantage gained in those years when it really was the only company that invested in the development of virtual solutions. Nowadays -whatever the vendor of my hypervisor might be- virtual machines, as a matter of fact, are the fundamental computing unit of an IT system.
However, something is deeply changing in IaaS architectures: we’re talking about two important innovations such as the development of applications built natively for a cloud architecture and containers, which radically simplify the implementation and the development of the more traditional applications. VMware is naturally working as quick as possible to maintain its advantage in this sector too.
Let’s see how by analyzing the solutions introduced during the last VMworld (Europe and USA).
Anatomy of a cloud-native application
According to Kit Colbert -VMware’s VP & CTO and Team Leader of the Cloud Native Application project- the term cloud-native is used for these last-generation applications built on top of dynamic and elastic infrastructures. Software defined datacenter, coupled with the infrastructural elements of the vSphere and NSX packages, is the ideal setting where to run traditional and cloud-native applications.
Read more ...
- Details
-
Published: Thursday, 10 December 2015 12:30
-
Written by Filippo Moriggia
During the last VMworld Europe we met and interviewed Robbie Wright, Commonvault Senior Manager Product Marketing, who was there with the full team in charge of the development of the products of the american company. We had a nice chat with him.

How would you define your product line? Isn’t it reductive to talk about just backup solutions?
Yes, lots of people identify us with backups, but Commonvault’s solution is so broad and advanced that we can define it better by using three terms: data protection, management and compliance. In particular, we believe that the idea of backup itself is obsolete, here at VMworld we are speaking of Workload Portability, the opportunity of transferring the entire workload among different cloud services. The whole infrastructure becomes a single thing for us.
Read more ...
- Details
-
Published: Tuesday, 10 November 2015 11:03
-
Written by Giuseppe Paternò
Previous article: OpenStack Components
Horizon – Dashboard
Horizon provides a modular web-based user interface for all the OpenStack services. With this web GUI, you can perform most operations on your cloud like launching an instance, assigning IP addresses and setting access controls.
Read more ...
- Details
-
Published: Tuesday, 10 November 2015 11:02
-
Written by Giuseppe Paternò
Previous article: OpenStack Introduction
OpenStack is a collection of open source technologies delivering a massively scalable cloud operating system.
OpenStack cloud operating system controls large pools of compute, storage and networking resources throughout a datacenter, all managed through a dashboard that gives administrators control while empowering their users to provision resources through a web interface.
We can think of it as software to power our own Infrastructure as a Service (IaaS) offering, like the one behind Amazon Web Services.
Read more ...
- Details
-
Published: Tuesday, 10 November 2015 10:53
-
Written by Giuseppe Paternò
I’ve been sitting in front of many European IT Managers and CTOs and when they want to hear from me about OpenStack or Cloud, most of the times they mean something different: customers want a VMware replacement for virtualization. The most audacious ones are willing to have a nice web interface to access their virtual machines and that’s it.
Cloud sounds like yet another marketing buzzword, it can mean just about anything or nothing at all. We are not discussing here what is the reason of walking away from VMWare, but the idea of the equation “Cloud=Virtualization” is pretty spread across all the customers. This is actually what some vendors tried to let you think of cloud.
While Cloud implies a virtualized environment, virtualization is not a cloud. Let me define Cloud using the NIST definition: “Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (ex: networks, servers, storage, applications and services) that can be rapidly provisioned and released with minimal management effort”.
Read more ...
- Details
-
Published: Tuesday, 10 November 2015 10:49
-
Written by Giuseppe Paternò
Previous article: OpenStack: a planet to discover
The great advantage of OpenStack is that the end customer can choose whether to use the reference implementations for each project or a vendor-specific implementation for each one. The promise of OpenStack is the interoperability amongst different components from different vendors or open source projects, giving the customer the choice to find out what is the best solution for their own needs.
OpenStack could bring the following benefits to you:
Read more ...
- Details
-
Published: Friday, 18 September 2015 17:28
-
Written by Davide Piumetti
In the cloud era defining the boundaries between what remans inside the house and what goes on the Internet becomes harder and harder.
The same applies to 1Backup, a backup software that can be used within the walls on a local storage, or off-premises, in Coretech’s cloud, the company that sells it in Italy.
1Backup is a product that has two distinct utilization categories: end users seeking an easy way to backup data and system administrators, Msp and IT services retailers wanting a well localized product to offer to their clients approaching offsite backup, outside the walls.
The sotware is based on an Agent that can be donwloaded and installed on every desktop or server device, Windows (XP to 10, Server 2003 to Server 2012 R2), Linux (official support only for CentOS and Red Hat) and Mac (10.5 to 10.10), and a web interface with which other users with limited space and number of agents can be created, or even other sub-admin users capable of creating other users.
Msp, resellers and IT managers can assign permissions to clients, employee, etc.
Read more ...
- Details
-
Published: Friday, 18 September 2015 15:31
-
Written by Alessio Carta
VMware vSphere, the leading virtualization platform in the market, has come to version 6.0, which was released in February 2015.
In this article we will provide an overview of the main innovations with some considerations based on use experience and an analysis of the set of problems that can arise with un upgrade from previous versions
UPDATE: vSphere 6.0 U1 here's the news
The new numbers
Improvements are naturally of computational nature, as we expect in every upgrade to a new version. New number indicate that a single instance of VMware vCenter can host as much as 1.000 ESXi hosts, 15.000 registered VMs and 10.000 simultaneously powered on VMs. Each host can support up to 1024 VMs, can handle up to 480 CPU (from which 4096 vCPU can be exploited) and 6TB of RAM, which can get up to 12TB with certified hardware. Host clusters’ numbers are akin to that increase: it is possible to have 64 hosts and 8.000 VMs per cluster.
Like every release of vSphere, this one introduces an higher virtual hardware level with version 11, which allows each VM to handle up to 128 vCPU and 4TB of memory.
Read more ...
- Details
-
Published: Wednesday, 16 September 2015 10:39
-
Written by Alessio Carta
Some months have been through since the release of VMware vSphere 6 and the first little update has been released (U1), but has really come the time to upgrade for those who have an infrastructure built upon vSphere? In order to help you with the decision, in addition to the considerations that you can find in this article, we present you all the news; we took in consideration both the availability of custom ESXi images for the various manufacturers machine and the support of the main backup software products. It is quite hard to think about switching to a new system if the backup software that is currently being used is not compatible yet.
Read more ...
- Details
-
Published: Wednesday, 02 September 2015 18:14
-
Written by Lorenzo Bedin
We have tried for you Windows Server 2016’s Technical Preview 3, whose release date is expected to be at the beginning of next year. Let’s see what are the principal new feature
Windows Server 2012 R2 successor, as it’s known to the insiders, has arrived to the final phase of its development: the third preview dedicated to developers and technicians has been released at the end of last August. Before analyzing some of the more advanced features, we’ll talk about the news on a graphical side: as it has happened before with the previous releases (2012, 2012 R2 and 8, 8.1), the server version presents a graphical interface (GUI, Graphical User Interface) that can be thought as wholly shared with the desktop version. The reference is of course to the newly-born Windows 10, so there’s no more space for Modern interface with full-screen Tiles or Charms Bar on the right. The classic Start menu returns and it’s restyled, a news that will be appreciated by most sys admins, in particular for remote control uses.
Read more ...