Author
Extreme Networks purchases Broadcom datacenter
Extreme Networks, a network solution company based in Jan José, California, is about to acquire Brocade’s datacenter for $55 mln (with additional bonuses for the following 5 years), as written in an official statement.
The acquisition will happen as soon as the Singaporean Broadcom will complete the $5,9 bld of Brocade. Brocade is a San José-based company that produces routers, switches and software solutions for datacenters, and owns Vyatta, the network devices OS at the basis of the one used by Ubiquity.
In the past months Extreme Networks purchased the LAN wireless market from Zebra Technology and is about to purchase the networking business of Avaya.
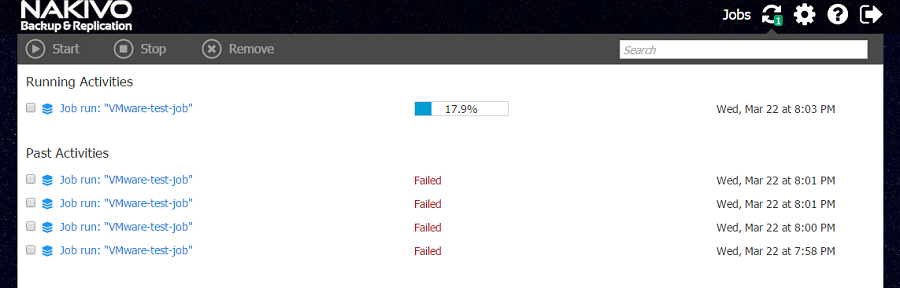
Read more Cloud and Datacenter Bulletin - April 2017The new version of the most renowned backup tool for virtual environments adds the support to vSphere 6.5 and improves the integration with the Microsoft world with the support to Hyper-V and Active Directory.
Nakivo Backup & Replication is a backup and Disaster Recovery solution for virtual machines that offers on-site and off-site backup (with testing), replication, recovery (even single files and Exchange/Active Directory elements), Cloud replica (AWS) and multi-tenant capabilities. We have tried in advance for you the new 7.0 version. You can find our review of the previous release at this address.
Support to vSphere 6.5 and Hyper-V
The new version of vSphere came out a couple of months ago and all big players are updating the support to the new release, and Nakivo makes no exception: now you can add an ESXi 6.5 host or vCenter 6.5 to the Inventory and protect all VMs running there. The new support to Hyper-V (version 2012, 2012 R2 and 2016) is with no doubts the most exciting news of Nakivo Backup & Replication 7: the support is extended to virtual machines created and managed with the popular hypervisor by Microsoft. Now the product can cover both main virtualization platform available in on-premises and Cloud infrastructures, also supporting an hybrid solution with the capability of backing data up to the public cloud by Amazon: AWS EC2.
Read more Nakivo: easy and flexible VMware and Hyper-V backupAmazon adds a Cloud region: Central Canada
Amazon announced at AWS Executive Insights a new AWS region called Central Canada with two Availability Zones, which adds to the regions already presents on the american soil: Northern Virginia, Ohio, Oregon, Northern California and AWS GovCloud, thus bringing to 15 the number or global regions with 40 Availability Zones.
Just last year AWS opened its first office in Canada, despite having tens of thousands of clients, and last august it added CloudFront sites in Toronto and Montreal to satisfy the request. The nes region will be hosted in Montreal data centers.
“For many years, we’ve had an enthusiastic base of customers in Canada choosing the AWS Cloud because it has more functionality than other cloud platforms, an extensive APN Partner and customer ecosystem, as well as unmatched maturity, security, and performance,” said Andy Jassy, CEO, AWS. “Our Canadian customers and APN Partners asked us to build AWS infrastructure in Canada, so they can run their mission-critical workloads and store sensitive data on AWS infrastructure located in Canada. A local AWS Region will serve as the foundation for new cloud initiatives in Canada that can transform business, customer experiences, and enhance the local economy.”
The new Central Canada is available for all AWS service including S3, EC2 and RDS. The first January 2017 a new AWS office in Dubai (United Arab Emirates) opened.
Read more Cloud and Datacenter Bulletin - January 2017WordPress 4.7.1 - Security and Maintenance Release is now available
Less than a month after the release of version 4.7 “Vaughan”, WordPress releases version 4.7.1 of the most used CMS in the world.
This is a “security and maintenance” release which fixes 8 important vulnerabilities that affect all WordPress versions (4. included), in addition to 2 bugs of the previous version.
The 8 vulnerabilities, which are now fixed, include cross-site scripting (XSS) and cross-site request forgery (CSRF) attacks.
The update is available at the administration dashboard and at the official Website. We encourage you to update your installation as soon as possible.
Read more CMS bulletin - January 2017WordPres 4.7.3 is now available
This is a “Security & Maintenance” release that doesn’t introduce any new feature, as it fixes bugs and problems available in the previous versions.
Because of the security-related fixes, we encourage you to update as soon as possible.
The previous versions had 6 big problems that have been completely fixed:
- Cross-site scripting (XSS) via media file metadata. Reported by Chris Andrè Dale, Yorick Koster, and Simon P. Briggs.
- Control characters can trick redirect URL validation. Reported by Daniel Chatfield.
- Unintended files can be deleted by administrators using the plugin deletion functionality. Reported by TrigInc and xuliang.
- Cross-site scripting (XSS) via video URL in YouTube embeds. Reported by Marc Montpas.
- Cross-site scripting (XSS) via taxonomy term names. Reported by Delta.
- Cross-site request forgery (CSRF) in Press This leading to excessive use of server resources. Reported by Sipke Mellema.
The update is available within the administration dashboard with an “Update Now” banner, or it can be performed manually; if you have enabled automated updates, your system will be updated soon.
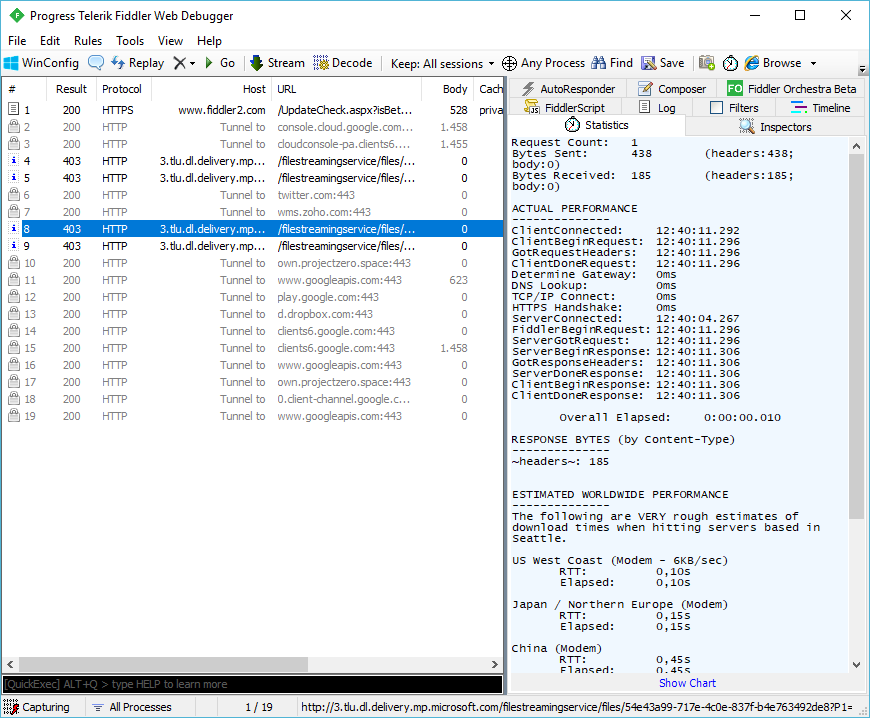
A vulnerability in Magento that allowed CSRF attacks has been discovered
A vulnerability that allows Cross Site Request Forgery (CSRF) has been discovered in Magento Community Edition (2.1.6 and older) by DefenseCode, which released a document covering the topic. The discovery followed an auditing on the source code of the Community Edition, the Enterprise version has not been tested (yet), but it’s possible that this version too is affected by this issue as both version share the most of the code.
The vulnerability exploits the option that allows admins to add Vimeo videos to product description; the system retrieves a preview image with a POST request accepting the image URL as parameter.
Such request can be changed to GET, and if the URL links to an invalid image file (like a PHP file), the system returns an error, however it downloading the file and not deleting it if validation fails.
Image information are analyzed and stored in a directory that follows a precise scheme: the pattern used is /pub/media/tmp/catalog/product/<X>/<Y>/<original filename>, where the path depends on the image name. For instance, picture.jpg creates the /pub/media/tmp/catalog/product/p/i/picture.jpg path.
Then two files are downloaded: one is the .htaccess file that enalbes the execution of PHP files in the directory, the other is the malicious PHP script.
A typical scenario involves an hacker targeting a Magento user with admin panel access (it can also be a non-full admin) with a phishing email with a link to a URL that starts the CSRF attack.
The “Add Secret Keys to URLs” option can mitigate attacks: you can enable it in Stores > Configuration > ADVANCED > Admin > Security > Add Secret Key to URLs.
Also disable the use of .htaccess files in the subdirectories of /pub/media/tmp/catalog/product/.
Magento developers stated this vulnerability will be fixexd in the next release of the CMS.
-
BYOD: your devices for your firm
The quick evolution of informatics and technologies, together with the crisis that mined financial mines, has brought to a tendency inversion: users that prefer to work with their own devices as they’re often more advanced and modern than those the companies would provide. Read More -
A switch for datacenters: Quanta LB4M
You don’t always have to invest thousands of euros to build an enterprise-level networking: here’s our test of the Quanta LB4M switch Read More -
Mobile World Congress in Barcelona
GURU advisor will be at the Mobile World Congress in Barcelona from February 22nd to 25th 2016!
MWC is one of the biggest conventions about the worldwide mobile market, we'll be present for the whole event and we'll keep you posted with news and previews from the congress.
Read More
- 1